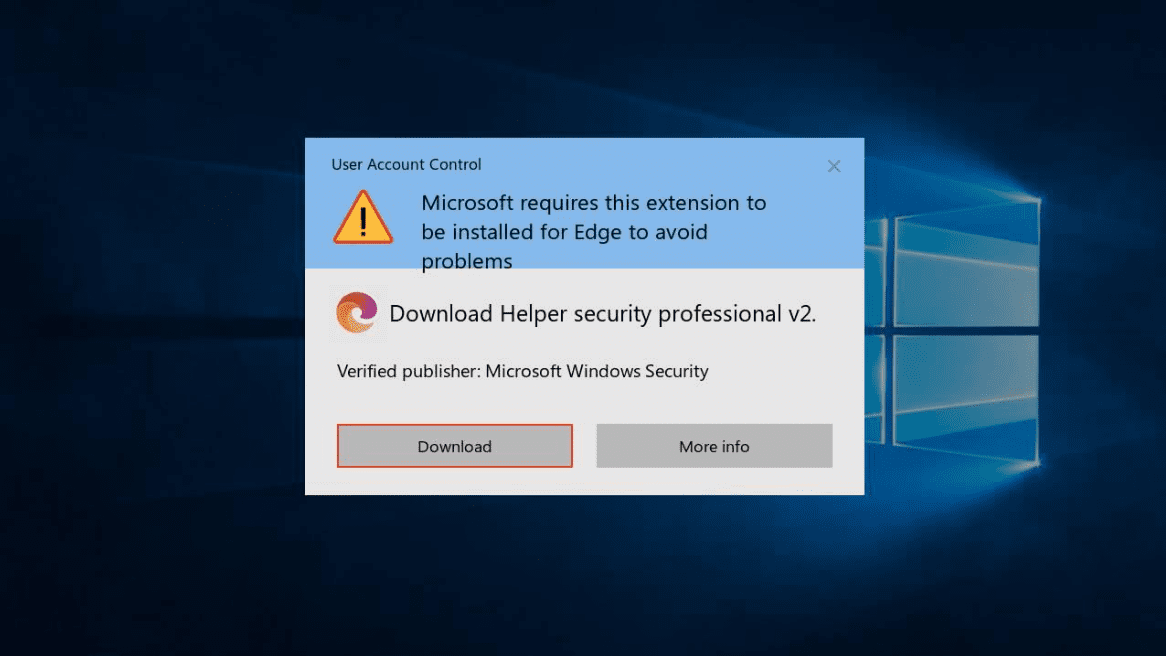
As the internet continues to evolve, browser extensions have become indispensable tools for enhancing productivity, improving user experience, and customizing browser functionality. However, not all extensions are created with good intentions. Malicious browser extension scams are on the rise, targeting unsuspecting users to steal personal data, spread malware, or compromise system security. In this article, we’ll explore how these scams operate, how to identify them, and the essential measures you can take to protect yourself online.
What Are Malicious Browser Extension Scams?
Malicious browser extensions are add-ons or plugins designed to appear legitimate but serve a hidden, harmful purpose. These extensions may:
- Steal Personal Information: Access sensitive data such as passwords, credit card numbers, or browsing history.
- Inject Ads or Redirect Traffic: Insert unwanted advertisements into websites or redirect users to phishing sites.
- Execute Malware: Act as a delivery mechanism for malware that can compromise your system or network.
- Monitor User Activity: Track keystrokes, mouse movements, and other activities to gather confidential information.
These extensions often disguise themselves as useful tools, such as ad blockers, productivity enhancers, or file converters, making it challenging to distinguish between legitimate and harmful plugins.
How to Spot Malicious Browser Extension Scams
Identifying a malicious extension is critical for your online safety. Here are some red flags to watch out for:
- Excessive Permissions Requests: Legitimate extensions usually ask for minimal permissions. If an extension requests access to your entire browsing history or permission to read and change data on all websites, proceed with caution.
- Poor Reviews or No Reviews: Check the user ratings and reviews on the browser’s extension store. Extensions with few or overwhelmingly negative reviews may not be trustworthy.
- Suspicious Developer Information: Legitimate developers often provide detailed information about their company or product. If the developer’s identity is unclear or seems fake, it’s best to avoid the extension.
- Unexpected Behavior: After installing an extension, if you notice unusual browser activity such as unexpected pop-ups, changes to your homepage, or sluggish performance, the extension could be malicious.
- Downloaded from Third-Party Sources: Always download extensions from official browser stores like the Chrome Web Store or Firefox Add-ons. Extensions from third-party websites are more likely to be harmful.
How to Protect Yourself from Malicious Extensions
Preventing malicious browser extension scams requires vigilance and proactive measures. Here’s how you can safeguard your online activities:
1. Stick to Official Sources
- Only install extensions from trusted browser stores.
- Verify that the extension is developed by a reputable company or individual.
2. Review Permissions Carefully
- Pay close attention to the permissions requested by an extension.
- Avoid extensions that demand excessive access to your data or browser.
3. Read Reviews and Ratings
- Check user feedback to identify potential red flags.
- Be wary of extensions with artificially inflated ratings or generic reviews.
4. Update Your Browser Regularly
- Keep your browser updated to ensure it has the latest security patches.
- An updated browser is more likely to block harmful extensions automatically.
5. Install Security Software
- Use reputable antivirus or anti-malware software to detect and remove malicious extensions.
- Enable browser-specific security features to prevent unauthorized installations.
6. Audit Your Installed Extensions
- Periodically review the extensions installed on your browser.
- Remove any extensions you no longer use or those with questionable functionality.
7. Educate Yourself and Stay Informed
- Stay up-to-date on the latest cybersecurity threats.
- Follow trusted tech blogs and cybersecurity forums to remain informed.
What to Do If You Suspect a Malicious Extension
If you believe you’ve installed a malicious extension, take the following steps immediately:
- Disable or Remove the Extension: Go to your browser’s settings and uninstall the suspicious extension.
- Clear Your Cache and Cookies: This can help remove any residual tracking scripts.
- Run a Security Scan: Use trusted antivirus software to check for malware or other threats.
- Change Your Passwords: If the extension accessed your accounts, change your passwords immediately, prioritizing sensitive accounts like email and banking.
- Monitor Your Accounts: Keep an eye on your bank statements, credit card activity, and other accounts for unauthorized transactions.
Conclusion
Malicious browser extension scams pose a significant threat to online users, but awareness and proactive measures can significantly reduce your risk. By staying informed, scrutinizing extensions before installation, and maintaining robust cybersecurity practices, you can protect yourself and your data from these evolving threats.
Stay safe online, and always prioritize your digital security!