DNS spoofing—also known as DNS cache poisoning—is a dangerous cyberattack in which attackers manipulate Domain Name System data to redirect your online traffic to malicious websites. This guide explains what DNS spoofing is, how it works, the red flags to watch for, and the key measures every online user can take to stay safe.
What Is DNS Spoofing?
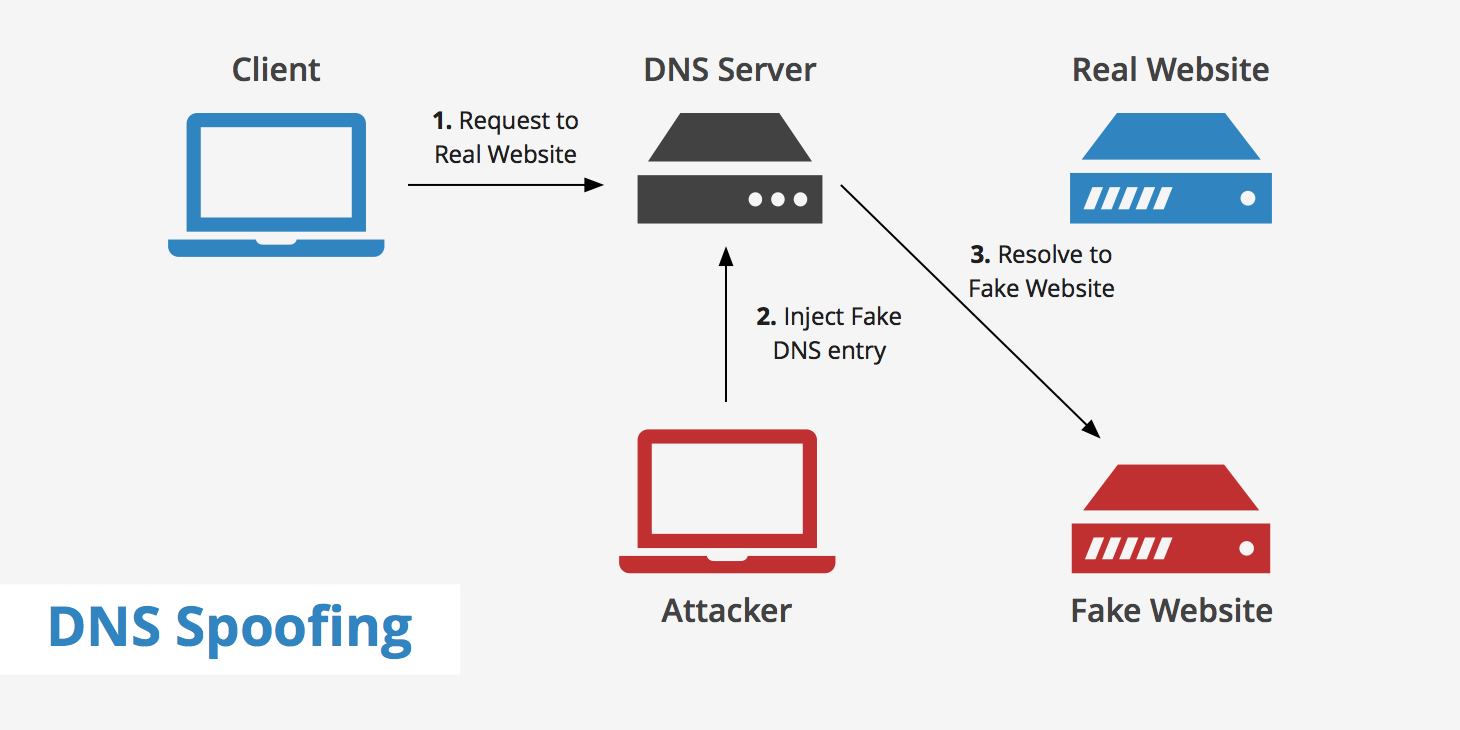
DNS spoofing is a cyberattack where attackers corrupt DNS data, so when you type in a familiar domain name (like example.com), the compromised DNS server returns an incorrect IP address. As a result, your browser connects to a fraudulent website that looks like the legitimate one, potentially exposing you to phishing scams, malware infections, and data theft.
Key terms: DNS spoofing, DNS cache poisoning, phishing, cyberattack
How Does DNS Spoofing Work?
DNS spoofing exploits vulnerabilities in the Domain Name System, which translates human-friendly domain names into numerical IP addresses. Here’s a simplified overview of the process:
- DNS Request Interception:
When you enter a website address, your device sends a DNS query to a resolver (often provided by your ISP). Attackers intercept this query using techniques like ARP spoofing or man-in-the-middle attacks. - Fake DNS Response:
The attacker quickly sends a forged DNS response before the legitimate response arrives. This fake response directs your device to the attacker’s server instead of the real website. - Cache Poisoning:
The malicious DNS response is cached by your device or the resolver, meaning future requests for that domain will automatically be redirected to the fraudulent IP address until the cache expires.
This process can occur in public Wi-Fi environments or compromised networks, making every user a potential target.
Common Techniques Used in DNS Spoofing
Attackers may employ several methods to execute DNS spoofing, including:
- ARP Spoofing:
By falsifying ARP (Address Resolution Protocol) messages, attackers can redirect traffic on a local network. - DNS Cache Poisoning:
This involves injecting false DNS records into a resolver’s cache so that subsequent requests are misdirected. - Man-in-the-Middle (MITM) Attacks:
Intercepting communications between your device and the DNS server allows an attacker to manipulate the DNS responses.
Understanding these methods helps in spotting anomalies and reinforces the importance of using advanced security measures.
How to Spot a DNS Spoofing Scam
Even the most cautious users can sometimes be redirected without immediate awareness. Here are some signs that your DNS might have been spoofed:
- Unexpected Website Behavior:
- The URL in the address bar appears slightly off (e.g., “examp1e.com” instead of “example.com”).
- The website’s design or layout seems different from what you normally expect.
- Pop-up warnings or unencrypted HTTP connections (lack of HTTPS padlock) appear unexpectedly.
- Suspicious Browser Warnings:
Modern browsers may warn you if a website’s security certificate is invalid or if you are connecting via an insecure connection. - Slow or Erratic Loading:
If familiar websites are loading unusually slowly or displaying error messages that suggest redirection, it could be a sign of DNS manipulation. - Phishing Prompts:
Be alert if you are asked unexpectedly to re-enter sensitive information, such as login credentials or financial data.
Regularly verifying website URLs and scrutinizing browser security cues can help detect potential DNS spoofing incidents before sensitive data is compromised.
Measures to Prevent DNS Spoofing
Taking proactive steps is key to minimizing the risk of DNS spoofing. Here are several best practices for online users:
1. Use Secure DNS Services
- Trusted DNS Providers:
Switch to reputable DNS services like Google Public DNS (8.8.8.8) or Cloudflare DNS (1.1.1.1), which are known for stronger security measures. - DNSSEC Implementation:
DNS Security Extensions (DNSSEC) add cryptographic signatures to DNS data, ensuring that responses are from legitimate sources and have not been tampered with.
rublon.com
2. Enable DNS over HTTPS (DoH) or DNS over TLS (DoT)
- Encrypt DNS Traffic:
These protocols encrypt DNS queries so that attackers cannot easily intercept or modify them. Check if your browser or network settings support DoH or DoT.
3. Keep Software Updated
- Regular Updates:
Ensure that your operating system, browser, and router firmware are up to date. Updates often include security patches that mitigate vulnerabilities exploited by DNS spoofing attacks.
4. Use Virtual Private Networks (VPNs)
- Encrypted Tunnels:
A VPN encrypts all your online traffic—including DNS requests—making it much harder for attackers to intercept or redirect your traffic on public networks.
5. Practice Cautious Browsing
- Verify URLs:
Always check the web address for typos or suspicious characters. Hover over links in emails and messages to preview the actual URL before clicking. - Look for HTTPS:
Confirm that websites use HTTPS and that the security certificate is valid before entering any sensitive information. - Multi-Factor Authentication (MFA):
Enable MFA on your accounts to add an extra layer of protection in case your login details are compromised.
Best Practices for Online Security
For further protection, consider the following habits:
- Educate Yourself and Others:
Stay informed about current cybersecurity threats and educate your peers on the signs of DNS spoofing and phishing scams. - Use Reliable Security Software:
Invest in reputable antivirus and anti-malware solutions that offer real-time protection and can detect unusual network activity. - Monitor Network Activity:
If possible, use tools to monitor your network’s DNS traffic. This can help detect any anomalies that might indicate a spoofing attempt.
Conclusion
DNS spoofing is a sophisticated and dangerous attack that can redirect you to malicious websites without your knowledge. By understanding how DNS spoofing works, being vigilant for red flags, and employing robust security measures such as secure DNS services, DNSSEC, VPNs, and cautious browsing practices, you can significantly reduce your risk of falling victim to this scam.
Staying proactive with your cybersecurity habits is key to protecting your personal data and ensuring a safe online experience.
For more detailed information and updates on DNS security, consider following reputable cybersecurity blogs and trusted sources.